YubiKeys are strange. Strange in the sense that they're a bunch of different devices all rolled into one neat & tiny package. Strange in that they offer so many different capabilities, and they're not exorbitantly expensive. Strange in that you'll find competing products charging the same price as a YubiKey but only offering just one of their capabilities.

This article will delve into the capabilities of YubiKeys, but in an enterprise context. Enterprise presents far more challenges for 2nd Factor Authentication (2FA), mainly because privacy is basically thrown aside when you're plugging in company YubiKeys into company computers, accessing company systems, and working in the company's interests.
FIDO2/WebAuthn/U2F
For some, this feature in YubiKeys is all that's needed to enable 2FA across the board, especially if your company is very cloud or SaaS-based. In fact if that's the case, then you can just buy the security key series for cheaper and go on your merry way.

FIDO/FIDO2/WebAuthn/U2F - these are all part of open standards designed by the FIDO Alliance to massively simplify authentication with tokens. They effectively took the best part of asymmetric cryptography and stripped out everything non-essential, leaving just the bare essentials for strong authentication to systems. FIDO2 does a little more than that, but the gist of what I'm about to say still mostly applies to it.
These standards do have their limitations though. For one, there's no identity (like a name) presented within the credentials, so you can't apply policies based on the credential presented, you must always instead build your authentication/authorization policies into your applications. And you can't revoke the devices remotely (unless you go and snatch it out of the user's hands!) - you must revoke the device (or user) within every application that the user has their token assigned to.
In the enterprise context you can overcome the limitations quite a lot by relying on a centralized Identity Provider, such as ADFS (+ Windows Hello for Business), to provide your authentication and authorization challenge point. If the device is just registered within the Identity Provider, then you can simply revoke it there to revoke access to all connected systems.
OTP
Yubico's OTP implementation is a little left-field. Most OTP implementations are what's known as "Time-Based One Time Passwords (TOTP)" - i.e. you have a token that generates codes every 30 or 60 seconds, and you need either a phone with an app for software-based tokens, or you buy one of the myriad hardware tokens on the market. Yubico's implementation instead uses a public identifier, password, and counter to generate single-use tokens.

The disadvantage here is that you still need a way to validate the OTP token codes. A user may insert their YubiKey and tap it to generate a code, but you then need to send that code somewhere to be verified. If you want complete 2FA coverage of your environment you'll have a lot of integration work to do.
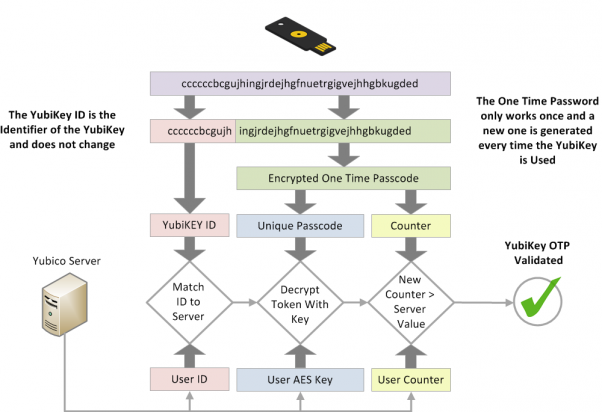
If you do get your hands on an Agent or service that can centralize the authentication with Yubico's OTP service, then you've got a 2FA capability that is just as simple and nice for the user as the U2F approach.
PIV
To be honest I was surprised when I first saw YubiKeys had a PIV smartcard in them. The PIV standard is fantastic, but most manufacturers default to adding a simpler (and cheaper) PKCS#11 smartcard to achieve almost exactly the same capability.
What does PIV offer above PKCS#11? Out-of-the-box compatibility. PIV, being a US Government standard designed for Government employees, has integrations that are already built into systems like Windows. PIV really is just an abstraction above PKCS#11, but it fixed a lot of the problems with the ambiguity in the PKCS#11 standard, thus negating the need to install hardware-specific drivers or middleware for every type of card you need to work with.
If you've ever tried integrating PKCS#11 cards, you'll know the horrors of trying to integrate them and why this standard is really that amazing...

Smartcards can be a little daunting - you can't just hand a new YubiKey fresh out of the factory to your users like you can for OTP or U2F. You need to provision them, and load them up first with PKI certificates, and lock them down, and get your users to pick a PIN for them.
Certificates are an underrated feature though (usually because they get put into the too-hard basket!). For instance, you can provision a YubiKey with certificates that enable:
- Authentication to Windows - both to desktop and remote sessions to servers for sysadmins,
- Authentication to Corporate VPNs - most products support certificates already,
- Authentication to Linux desktops and servers (but that's not as out-of-the-box as Windows),
- Digitally signing documents and emails (so you can stop wasting paper hand-signing things!),
- Encrypting documents and messages (keep your Intellectual Property or sensitive info out of other's hands), and
- Authentication to buildings (although that can get a little tricky if you need to replace your Physical Access System to work with YubiKeys, but most vendors now work with them).
- Authentication to partner organisations. With certificates you can set up trust relationships with other organisations, so your users can present their identities to other partner networks to gain access without the partner network needing to touch your company's YubiKeys.
These features are amazing, but you need tools to set all of this up, connecting your user's identities and the PKI that issues the certificates to the YubiKeys, and locking down each device so the user's PIN can't be reset on them and their credentials misused.
Oh yeah, we built that tool. You can get it by clicking here. It's probably the cheapest on the market too.
PGP
A little lesser-known to the general public, but YubiKeys support the PGP standard to digitally sign and encrypt content. I won't delve into this for the Enterprise context, because I really haven't seen many large businesses using PGP. It's more of an individual tool, and usually needs a technical user to work it because it's, well, complicated (to put it politely). The problems with handling PGP in the enterprise world have been solved by the PIV standard, as long as you're willing to deal with the extra baggage that brings.
BIO (Soon)
Yubico have done something amazing and put a fingerprint reader into a YubiKey. It's not out yet, but it'll open the door for even more integration opportunities in the future. Bio-metric support gets a bit tricky in the Enterprise world (especially if your users think that copies of their fingerprints are being held by the company), but it affords great opportunities for users to be able to prove their identity for specific contexts, like proving who they say they are for resetting a password.
I wouldn't recommend reliance on bio-metrics for strong authentication, but it's great as part of a larger 2FA solution for your business.
Yubineeding Yubikeys
If you haven't yet tackled the 2FA problem for your organisation, then you've got a gaping wide hole in your network - even if your network is airgapped and standalone. YubiKeys are the fastest and probably easiest first step you'll take to enable 2FA everywhere, and you can use Signata Enterprise to make yours and your sysadmin's lives easier with distributing and managing them.





